Webshells automating reconnaissance gives us an easy detection win
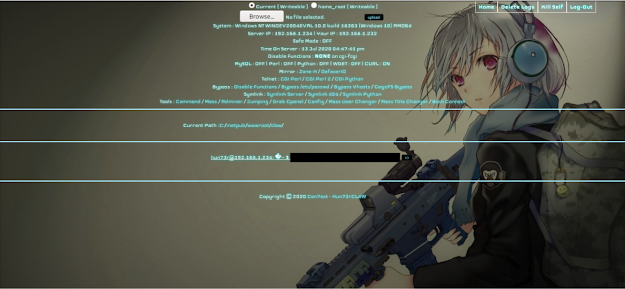
For those following along with ATT&CK this entry is about Server Software Component: Web Shell which is now a sub-technique of T1505, specifically it is T1505.003. If I can avoid combing through web access logs to find stuff like webshells I'll happily dodge it, having looked at the log artefacts left by a number of popular public domain webshells I've found a couple of easy detections based around Windows Event Log (WinEventLog). We're looking at webshells like "Con7ext", variants of "WSO" and "Alfa Shell": Specifically we are looking at the parts of the webshell that provide basic reconnaissance as to server components and functionality: How is the webshell checking if perl, python or wget are installed? In a rather noisy way that we can definitely hunt for: For IIS and a PHP shell the Splunk SPL to search for this looks something like: index=win10 sourcetype="WinEventLog:Security" EventCode=4688 Account_Name=IUSR Creator_P...