Webshells automating reconnaissance gives us an easy detection win
For those following along with ATT&CK this entry is about Server Software Component: Web Shell which is now a sub-technique of T1505, specifically it is T1505.003.
If I can avoid combing through web access logs to find stuff like webshells I'll happily dodge it, having looked at the log artefacts left by a number of popular public domain webshells I've found a couple of easy detections based around Windows Event Log (WinEventLog).
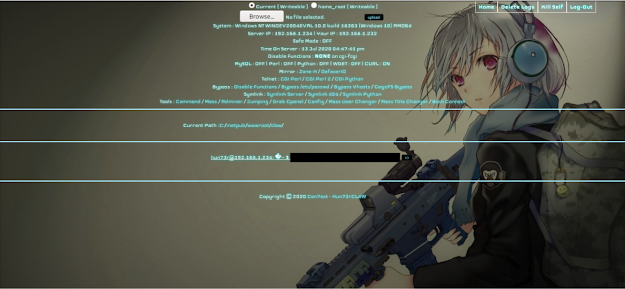
We're looking at webshells like "Con7ext", variants of "WSO" and "Alfa Shell":
Specifically we are looking at the parts of the webshell that provide basic reconnaissance as to server components and functionality:
How is the webshell checking if perl, python or wget are installed? In a rather noisy way that we can definitely hunt for:
index=win10 sourcetype="WinEventLog:Security" EventCode=4688 Account_Name=IUSR Creator_Process_Name="*\php-cgi.exe" New_Process_Name=*\cmd.exe AND (Process_Command_Line="*help*" OR Process_Command_Line="*-h*")| table _time Account_Name Creator_Process_Name New_Process_Name Process_Command_Line
So what's going on with this SPL? Let's have a look.
We are looking for the IIS web user (IUSR) and EventCode 4688 (process creation) for cmd.exe processes spawned by php-cgi.exe that include the strings we are looking for ("help" or "-h"). You'll see these three process all spawn within a minute of each other.
The good thing about this detection is that for certain webshells these commands run automatically to populate the informational part of the webshell UI, so traces are left no matter how careful the adversary using the shell is.
Happy hunting!